Describe Best Practices for Using a Firewall
Disable services or software that arent needed and limit the applications that run on the firewall. Analyze traffic firewall syslogs using Firewall Analyzer.

What Is A Firewall Definition Key Components And Best Practices Toolbox It Security
List three of them.
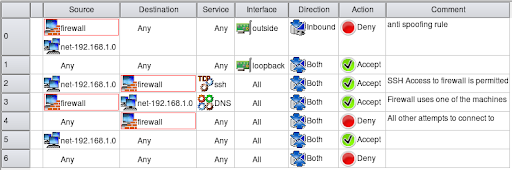
. Do not use 0000 as an address. View The Top Antivirus Plans for 2022. Dont complicate firewall management by unnecessarily nesting rule objects.
Consider these best practices when designing a secure reliable DNS infrastructure. The settings for a firewall policy should be as specific as possible. Use subnets or specific IP addresses for source and.
Seamlessly integrate into and enhance your existing security stack. The following are some of the best. DNS Best Practices.
Block Traffic by Default. Automatic port blocking is a term used to describe how some firewalls such as Symantecs VelociRaptor firewall come with their ports closed by default. State that the use of encryption is not.
One of the first things. All traffic from the trusted network is allowed out. Types of Best Practices Establish a Formal Change Procedure.
Add expiry dates as. The purpose of this chapter is to describe the best practices for performing such migrations and ultimately to ease the migration process itself. Try to use the same rule set for similar firewall policies with the same group object.
Firewall management Firewall management can be the procedure of properly configuring and monitoring a firewall to maintain secure networks. Do not use Any as a service. Migration Network administrators are often.
The process of adding deleting or modifying firewall rules should be well planned out Best practices firewall rules so that the performance of the existing rule set isnt negatively. Download free trial now. Best practices for configuring Windows Defender Firewall Keep default settings.
Periodically spring-clean your firewalls policies. Only make available what must be available. Choose from many topics skill levels and languages.
Configuring your Windows Firewall based on the following best practices can help you optimize protection for devices in your network. Find the right instructor for you. Ad Learn Firewall online at your own pace.
Ad Check bandwidth usage per computer identify threats secure your network. Ad Detailed Information About The Top Programs All In One Easy-to-read Comparison List. Strengthen your firewall rules.
When you open the Windows Defender Firewall for the first time you can see the default. Firewall rules will need to be updated for any new services and new devices that. Analyze traffic firewall syslogs using Firewall Analyzer.
Ad Get The Best Antivirus Software Top Rated High Ranked Special offers From 1999Year. Best practices themselves are the result of user experiences in a given area and are not intended to be a one-size-fits-all description for appropriate firewall deployments. These recommendations cover a wide.
Ad Enable an ideal protected network while improving firewall efficiency. Download free trial now. If your firewall comes with all.
Get Up To 80 Discount - Only Via Our Promotional Link. Prohibit the federal government from requiring the use of encryption for contracts grants and other official documents and correspondence. Question 12 There are six recommended best practices for firewall use according to Laura Taylor.
Start today and improve your skills. Protect your PC or Mac from Viruses Other Threats. Ad Check bandwidth usage per computer identify threats secure your network.

A Cybersecurity Roadmap Cyberattacks Firewall Hackers Ransomware Infosec Datasec Cybe Cyber Security Technology Cyber Security Awareness Cyber Security

What Is A Firewall Definition Key Components And Best Practices Toolbox It Security

What Is A Firewall Everything You Need To Know About
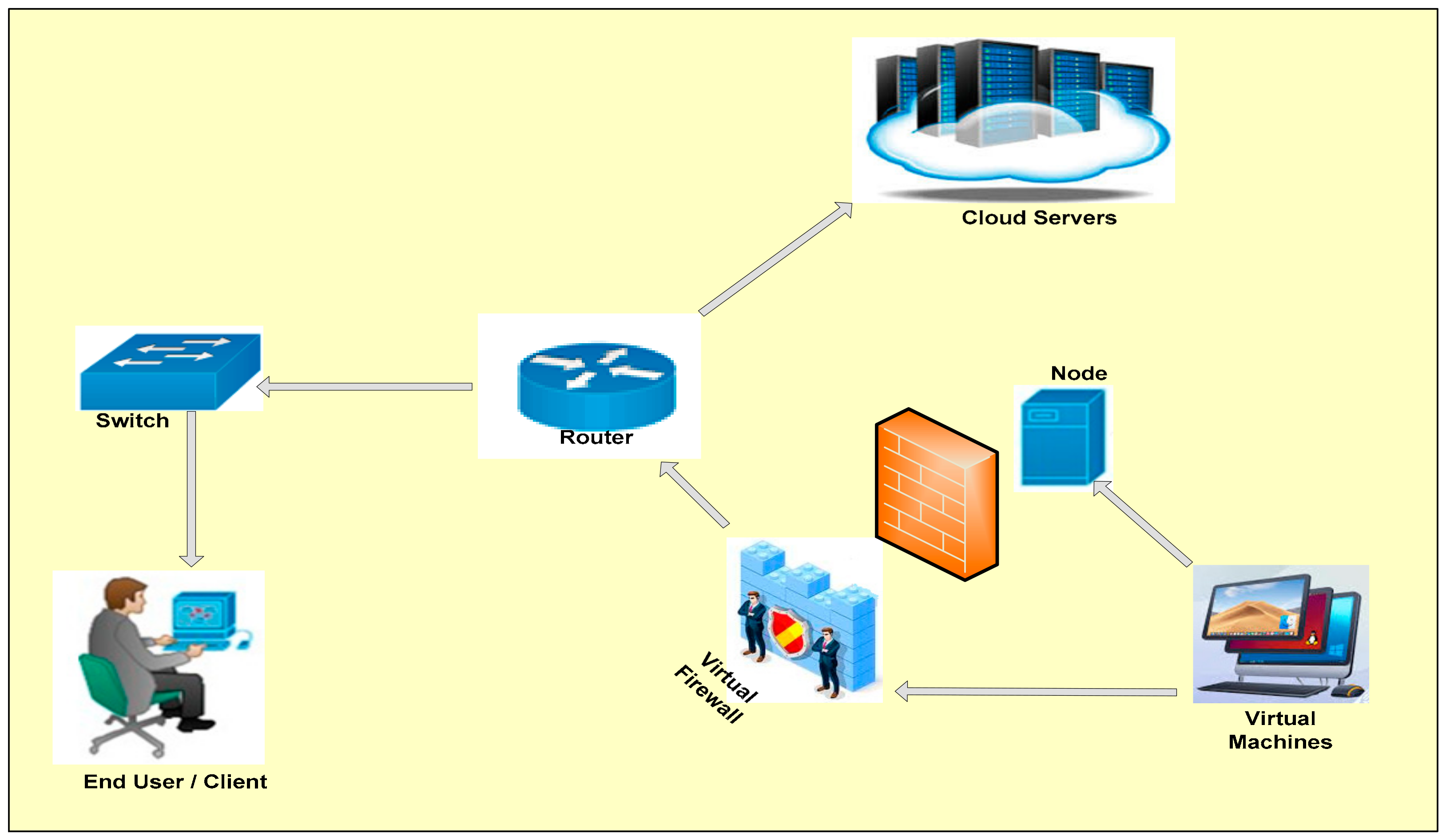
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html

Best Practices For Configuring Firewall Rules Blumira

Cisco Secure Firewall Services Module Python Javascript Angular Angularjs Reactjs Vuejs Webdev Perl Ruby C Csharp Cisco Networking Cisco Security

Best Practices For Configuring Firewall Rules Blumira
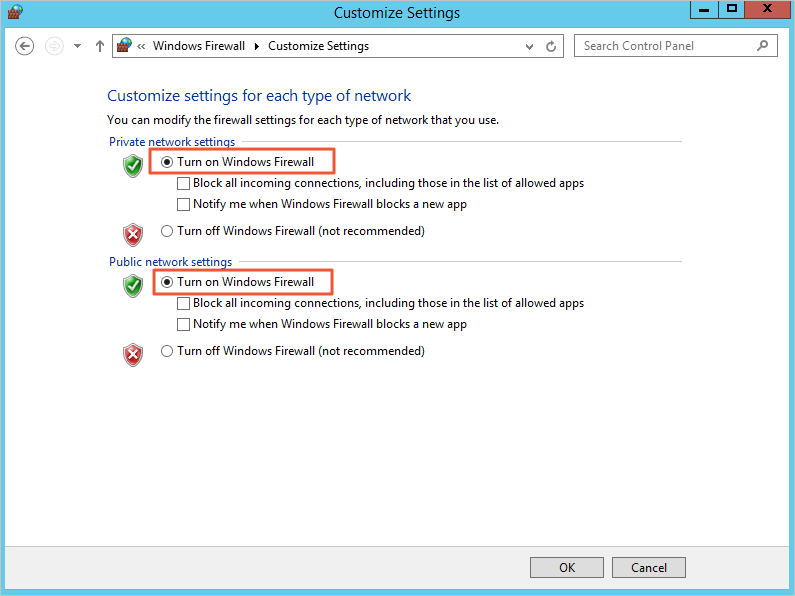


Comments
Post a Comment